Hello Guys , Welcome To USER-X ,
We're back with another cool trick for all the android users.
So most of you might be using an Android Phone from a long , and it always boots up with the same screen as when you turn it on from switch off state, Right?
So , it might be a boring way , or you may have fed up with that old thing, so
Do you wanna try one ?
So this trick is for all geeks out there, who want to try something new.
So what is Boot screen ?
Ans :- The boot animation is the first thing that you see when powering on your Android phone or tablet, after the operator or manufacturer logo. Although it does not serve a purpose functionally, an eye-catching boot animation can certainly make your device stand out while booting. In this third installment of our Android customization series, we will take a look at how to change or even create your Android boot animation and will feature some of the prettiest and geekiest boot animations we have come across
Tools You Need to Change Boot Screen?
Ans :- 1. Rooted mobile phone(No idea what Rooted Phone is ? Get it from Here. Just download and click on root now! )
2.ES file Explorer
Step 1. Download the boot repositories from here , and make sure to download the correct resolution from Here.
Step 2. Now open ES File Explorer and ensure you have enabled root explorer in its settings. Navigate to the folder /system/media and you will find a file named bootanimation.zip. Rename it as bootanimation.zip.bak. This will help you to revert to stock animation in the future. Having done that, paste the bootanimation.zip file that you downloaded from the internet to /system/media.
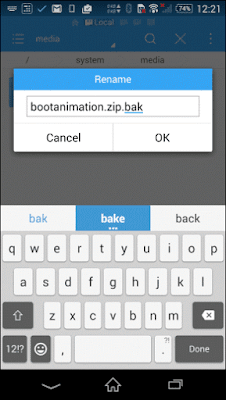
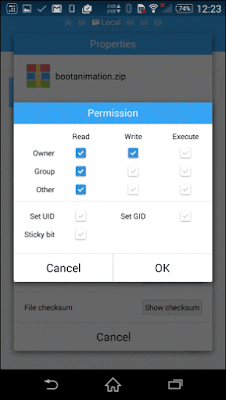
Step 3. One last thing before you reboot would be to fix the file permission. Long tap on the new bootanimation.zip file and change the permissions to rw-r—r—and save the settings.
Step 4. Now you're Done. Now when you reboot your phone, you will have your new android boot animation ready for you.
Note: Before rooting and trying these all tricks above , you might be aware of rooting a mobile phone and using tools after rooting your phone.












.jpg)




